Hi all,
mitigating the Secure Boot UEFI bootkit using the May 2023 cumulative update still causes misunderstandings at some of my customers. So I wrote this short article to give you an overview and illustrate how this update works, especially regarding the elemination of the BlackLotus bootkit, covered in CVE-2023-24932. A very detailed description can be found in the official KB article: KB5025885 support page.
Among many other fixes, this update adds protection against a Secure Boot security feature bypass of the BlackLotus UEFI bootkit tracked by CVE-2023-24932. However, some steps to fully mitigate the vulnerability must be performed manually. For easier understanding, let me first divide the May 2023 CU into 2 steps:
- Install the CU to apply all the monthly security fixes, update the boot files of the running OS and copy the UEFI Code Integrity boot policy file to the harddrive.
- Manually copy the Code Integrity boot policy to the EFI partition and apply the UEFI block list
Step 1 only affects the running operating system while step 2 modifies the UEFI of your PC. This is important because the 2nd step has to be done manually at the time of writing. Later CUs will simplify this part. Following illustration may help.
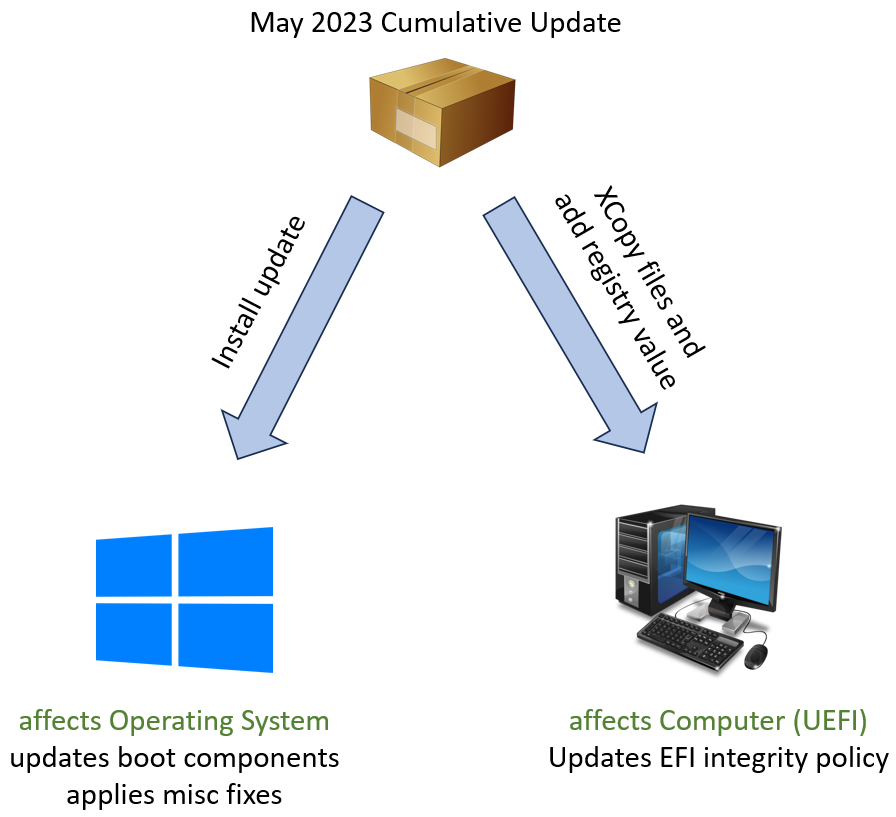
Install the CU
Installing the CU updates the boot components of the running operating system or an offline image, if you slipstream the update into it. As a part of the CU installation, files necessary for the UEFI patch (2nd step) are copied to the hard drive to %systemroot%\System32\SecureBootUpdates. However, the update installation process does not acitivate the UEFI patch, which means, it does not copy those files to the EFI partition so the PC remains vulnerable against the CVE-2023-24932 bootkit.
If you just install the CU using Windows Update, WSUS or any other method, all fixes will be applied to the OS but the UEFI of the PC remains unpatched. In that case, both, updated and unpatched images will boot from that PC.
Please note, that we always recommend to roll out monthly cumulative updates as soon as possible!

Install the UEFI patch
Applying the UEFI patch requires you to add the code integrity policy to the EFI partition. The CI policy file, you need for this step, was copied to the system as part of the CU installation. As mentioned before, I will not cover the technical details in this blog post. See chapter 3a within the KB5025885 support page for technical instructions. Secondly, the UEFI deny list needs to be applied. This is done by adding a registry key to the patched OS, followed by a reboot. Technical instructions can also be found in the KB article, chapter 3b.
After the PC’s UEFI has been patched, the vulnerability for the BlackLotus bootkit has been mitigated. However, this PC does not longer boot unpatched operating systems (meaning OS with boot files from before the May 2023 update).
Please note, that all bootable operating system images need to be patched after the 2nd step (UEFI patch) has been applied, in order to make them work on UEFI patched PCs. This includes running operating systems, custom Windows images, Windows PE boot images, Windows SafeOS Recovery Environment (WinRE) and all recovery media. There will be Dynamic Updates for WinRE since there are known issues when trying to apply the full CU.

Best practice for enterprises
I suggest to follow the rough approach below. Note, that only after finishing step 3 your PC is fully protected against the Secure Boot bypass vulnerability.
- Patch all running operating systems with the May 2023 CU or later. Do not apply the UEFI patch part yet. Only install the CU.
- After that or at the same time, make sure to patch all Windows PE and Windows images you use for fresh installations. You can use DISM to “slipstream” the patch into the images. See Appendix B in this post for a rough explanation. If you’re using Windows Recovery Environment (WinRE), those images must be patched as well. Please use the corresponding Dynamic Updates in the context with WinRE.
- As a last action, apply the UEFI patch on all running systems by following the steps 3a and 3b of the KB article mentioned at the beginning of this blog. For automation you can write a batch file and deploy it using your system management tool.
Appendix A – Download a cumulative update
Navigate to the Microsoft Update Catalog to download the latest cumulative update in MSU file format. In the search field enter
2023-05 22H2
to narrow down the search results. Find your desired update in the list and click the Download button.
Appendix B – Update a custom Image using DISM
There are tons of examples of how to update offline images available in the web. So I do not spend too much time for explanation. Use these lines just as a reference. Please note that you may need to change some values to fit your environment:
mkdir C:\Mount DISM /mount-wim /wimfile:“C:\Path\To\Install.wim“ /mountdir:C:\Mount /index:3 DISM /image:C:\Mount /add-package /packagepath:“C:\Path\To\Update.msu“ DISM /unmount-wim /mountdir:“C:\Mount“ /commit rmdir /Q /S C:\Mount

Leave a Reply
You must be logged in to post a comment.